Comprehensive Security and Alert Management System
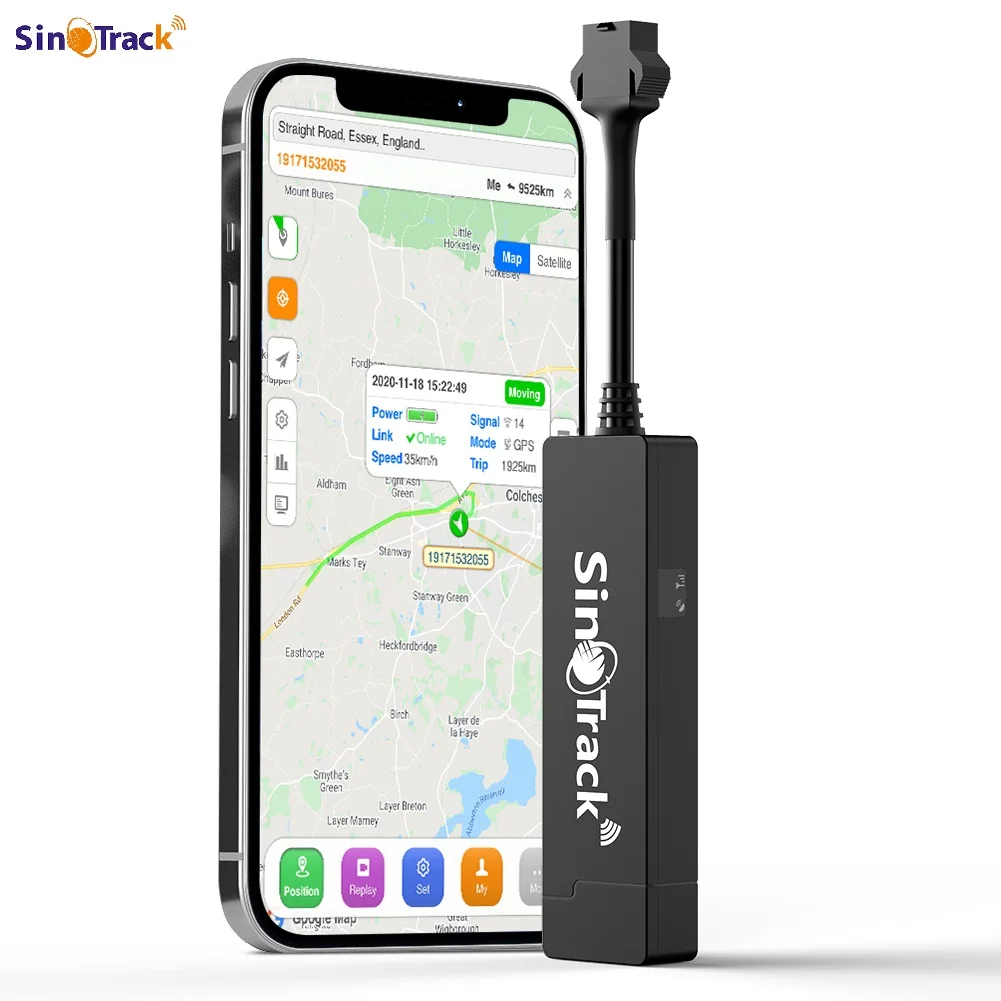
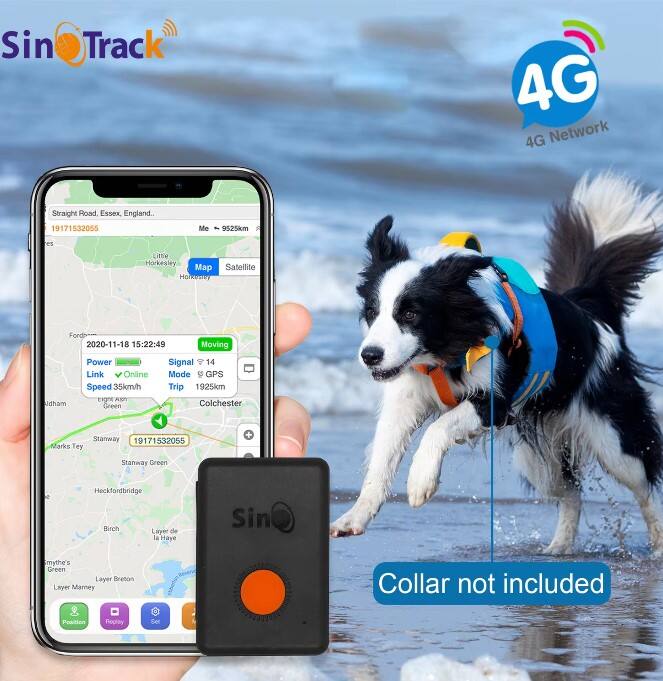
The portable location tracker features an intelligent security framework that provides multi-layered protection against theft, tampering, and unauthorized access while delivering immediate notifications for various emergency and security scenarios. Sophisticated motion detection algorithms can distinguish between normal handling and suspicious activities such as forced removal, tampering attempts, or unauthorized movement patterns. The device generates instant alerts through multiple communication channels including SMS, email, push notifications, and phone calls, ensuring users receive critical security information regardless of their preferred communication method. Geofencing capabilities allow users to establish virtual boundaries around specific locations, automatically triggering alerts when the portable location tracker enters or exits designated areas. The system supports unlimited geofence zones with customizable shapes, sizes, and time-based activation schedules, accommodating complex monitoring requirements for businesses, families, and personal security applications. Tamper detection sensors identify attempts to disable, remove, or damage the device, immediately notifying users and activating enhanced tracking protocols to maintain location visibility even during security breaches. Emergency features include panic button functionality that allows users to trigger immediate distress signals with precise location information, potentially saving lives during medical emergencies, accidents, or dangerous situations. The portable location tracker maintains encrypted communication protocols that protect location data and personal information from interception or unauthorized access during transmission and storage. Stealth mode capabilities allow the device to operate silently without visible indicators, making it difficult for thieves or unauthorized individuals to detect the presence of tracking technology. Advanced alert filtering prevents false alarms by analyzing movement patterns, environmental factors, and user behavior to distinguish between genuine security threats and normal activities. The system provides detailed incident reports that include location history, timeline analysis, and supporting data to assist law enforcement and insurance investigations when theft or other security incidents occur.