Comprehensive Security Features with Multi-Layer Protection
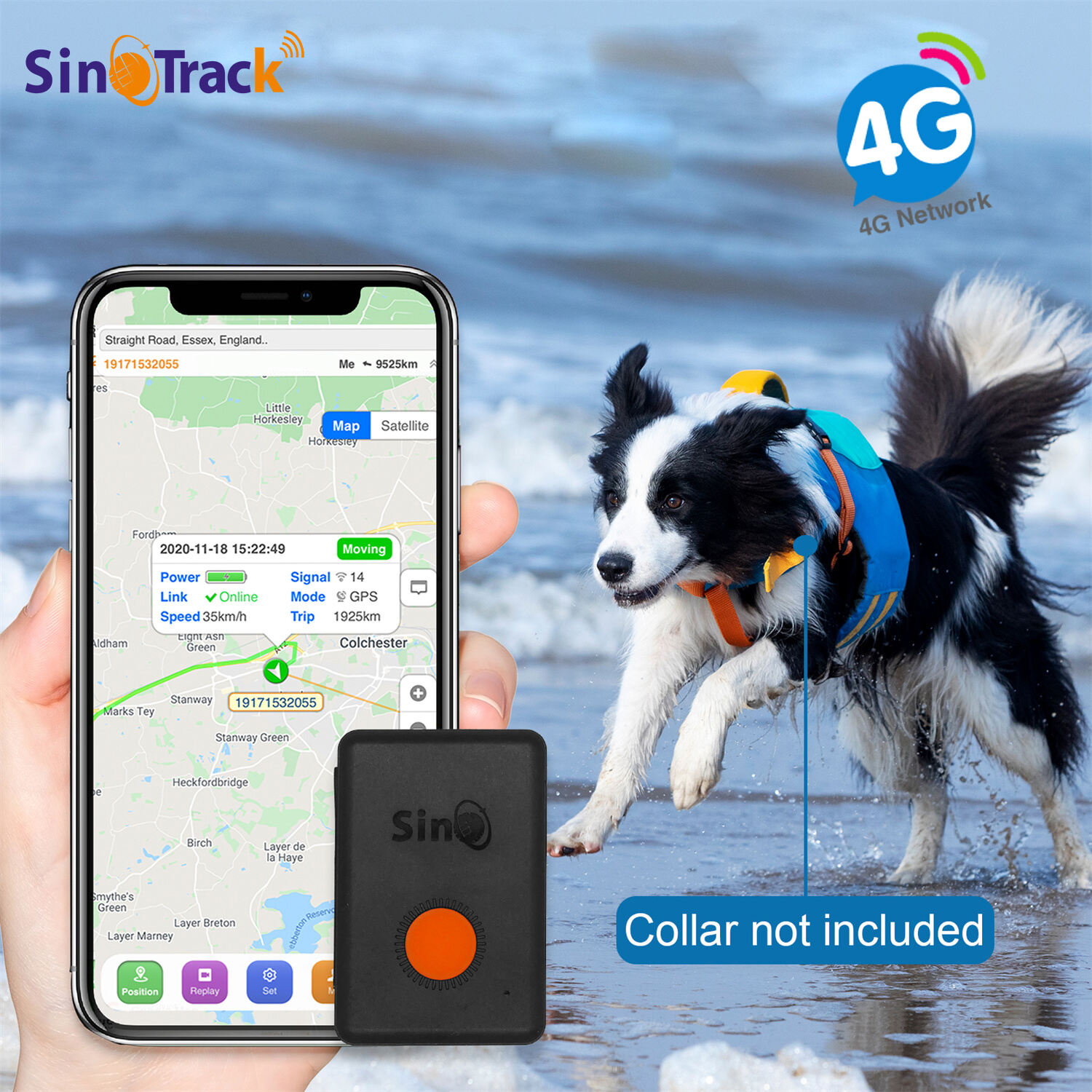
The 4G GPS locator provides robust security measures that protect both the device and transmitted data through multiple layers of advanced protection systems. Encrypted communication protocols ensure all location data transmits securely between the device and monitoring platforms, preventing unauthorized access or data interception by malicious parties. The security architecture employs military-grade encryption standards that continuously evolve to address emerging cyber threats and maintain data integrity. Tamper detection systems within the 4G GPS locator trigger immediate alerts when unauthorized individuals attempt to remove or disable the device, providing early warning of potential security breaches. These sophisticated sensors monitor device orientation, vibration patterns, and housing integrity to detect tampering attempts with high accuracy while avoiding false alarms from normal operational conditions. Geofencing capabilities create virtual boundaries around specific locations, automatically sending notifications when tracked objects enter or exit designated areas. This feature proves invaluable for monitoring unauthorized vehicle use, ensuring children remain within safe zones, or protecting valuable assets from theft. The 4G GPS locator supports multiple user access levels with customizable permissions that control who can view tracking data and modify device settings. Administrative controls enable managers to grant specific employees access to relevant tracking information while restricting sensitive configuration options to authorized personnel only. Anti-jamming technology protects against GPS signal interference attempts, maintaining tracking capability even when hostile parties attempt to block satellite communications. The device automatically detects jamming attempts and switches to alternative positioning methods while alerting users to potential security threats. Remote configuration capabilities allow administrators to modify security settings, update firmware, and adjust operational parameters without physical access to devices, enabling rapid response to security concerns or changing operational requirements. Audit trails maintain detailed logs of all device interactions, configuration changes, and access attempts, providing comprehensive records for security analysis and compliance requirements.